Defensive Cyberspace Operations Division (DCO-D)
US Army Regional Cyber Center – CONUS
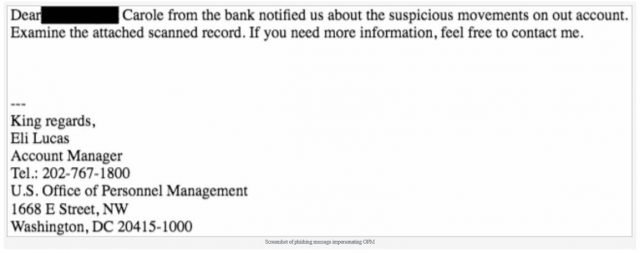
Department of Defense personnel are being targeted by an email phishing attack disguised as a warning letter from the US Office of Personnel Management (OPM) regarding fraudulent bank account activity.
OPM does not monitor DOD members’ bank activity.
Computer users should be wary of opening file attachments received via email, especially from outside their immediate organization.
The latest form of ransomware targeting DOD is called “Locky” because it renames file extensions to “.locky” after encrypting them. Other popular ransomeware includes “Zepto” and “Odin.”
The ransomware displays a message that a decryption key can be purchased through a web site, typically using a payment system that is extremely difficult to trace.
Here is one example of the email. As noted by the phishme.com website, there is strange wording within this email that should raise suspicions such as “suspicious movements” and “out account”.
 Recommendations:
Recommendations:
- If there is any doubt about the authenticity of an email urging you to open an attachment do not open it, it’s better to be safe than sorry.
- Understand that the perpetrators of this campaign are attempting to use fear to trick individuals into executing this payload.
- If you had previously agreed to identity monitoring as provided by OPM check your records to determine which company is providing this service to you and contact them directly regarding their monitoring activities.
